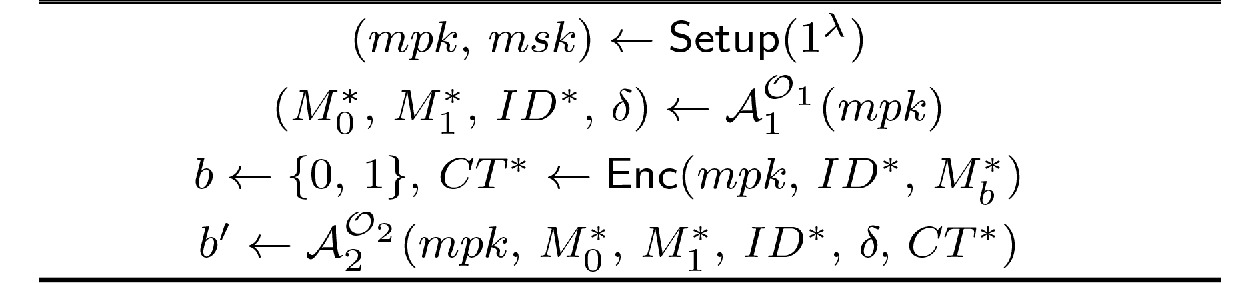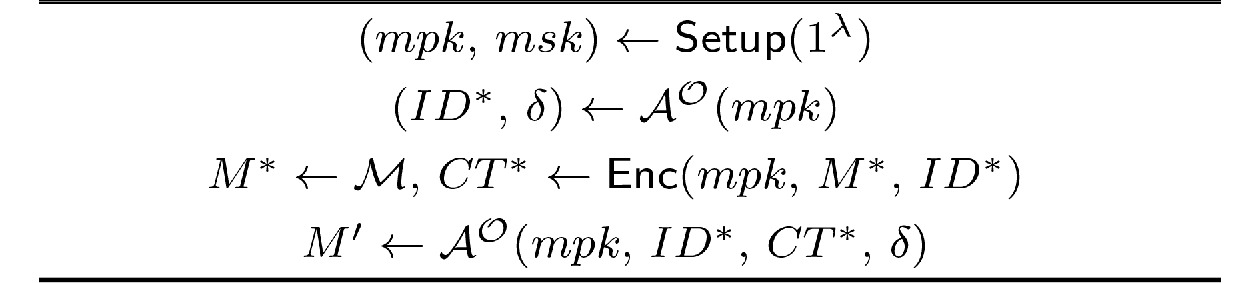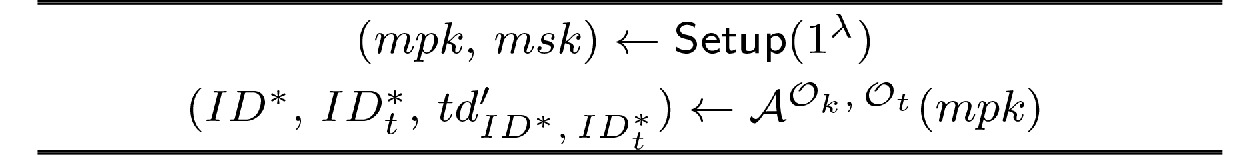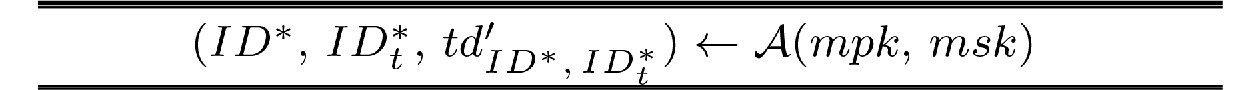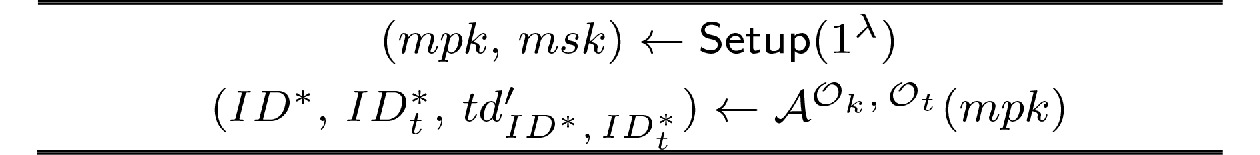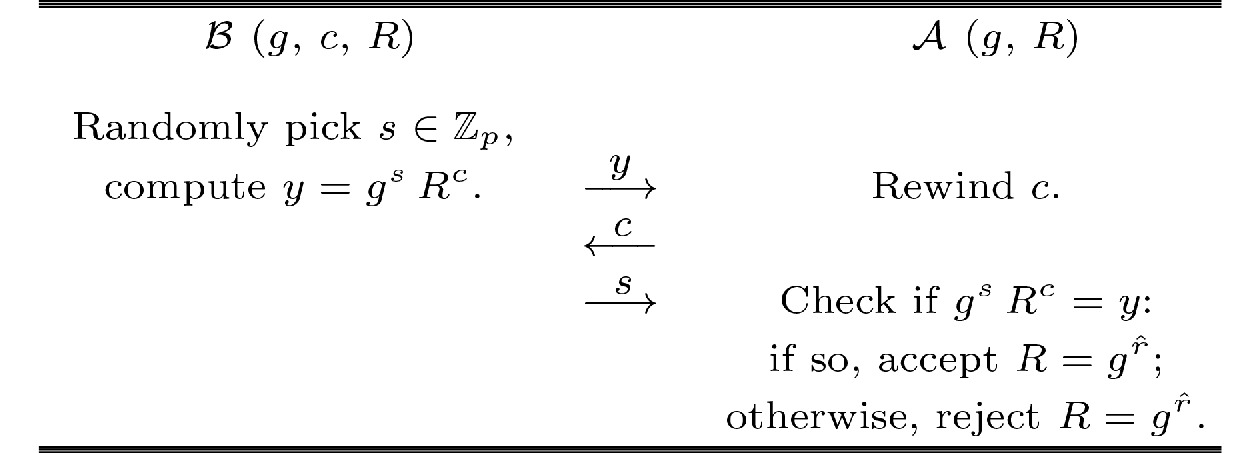Figures of the Article
-
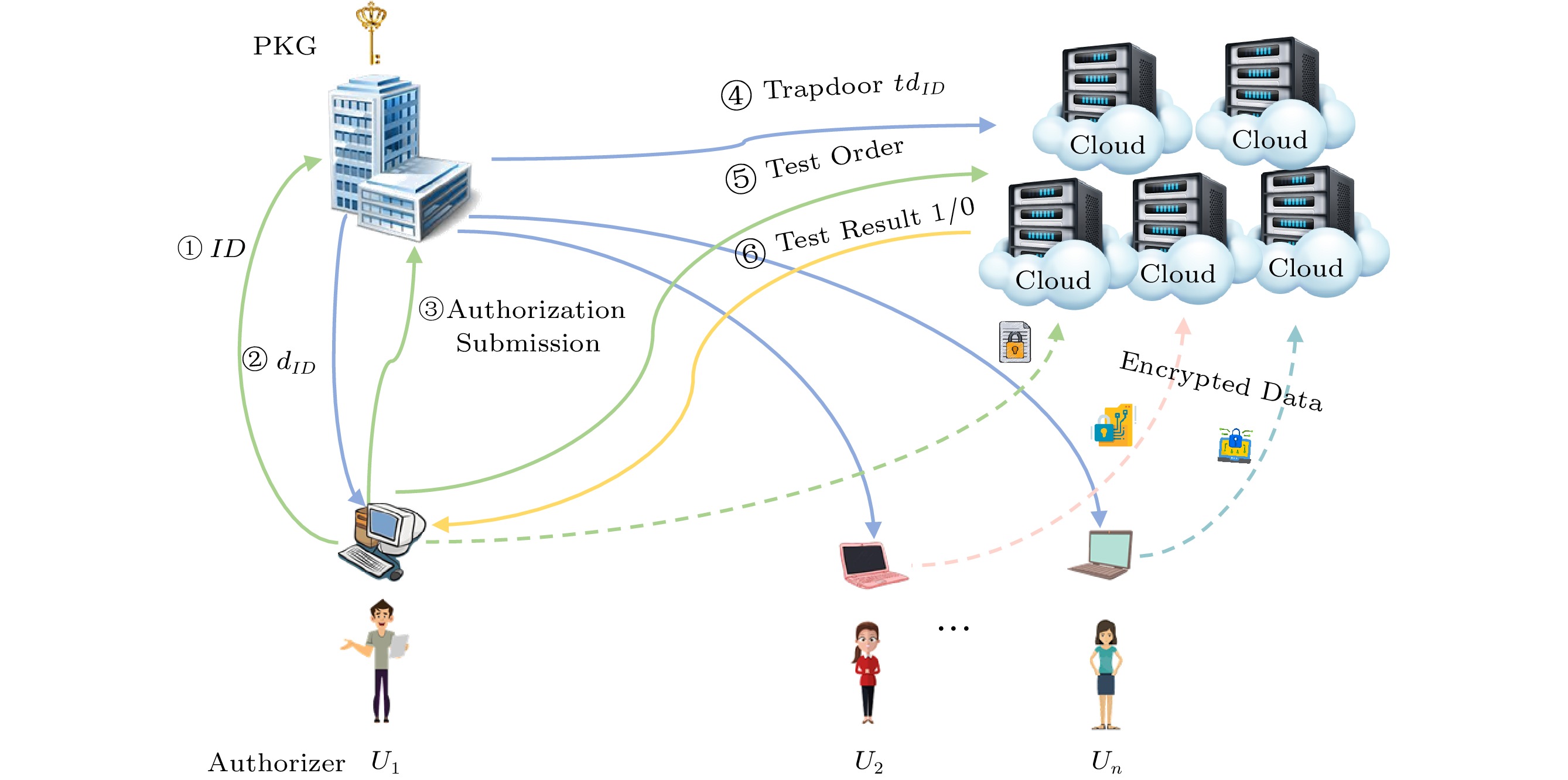
![]() System model of IBEET in cloud computing. dID: the private key of the authorizer U1 with ID. tdID: the trapdoor of the authorizer U1 with ID.
System model of IBEET in cloud computing. dID: the private key of the authorizer U1 with ID. tdID: the trapdoor of the authorizer U1 with ID.
-
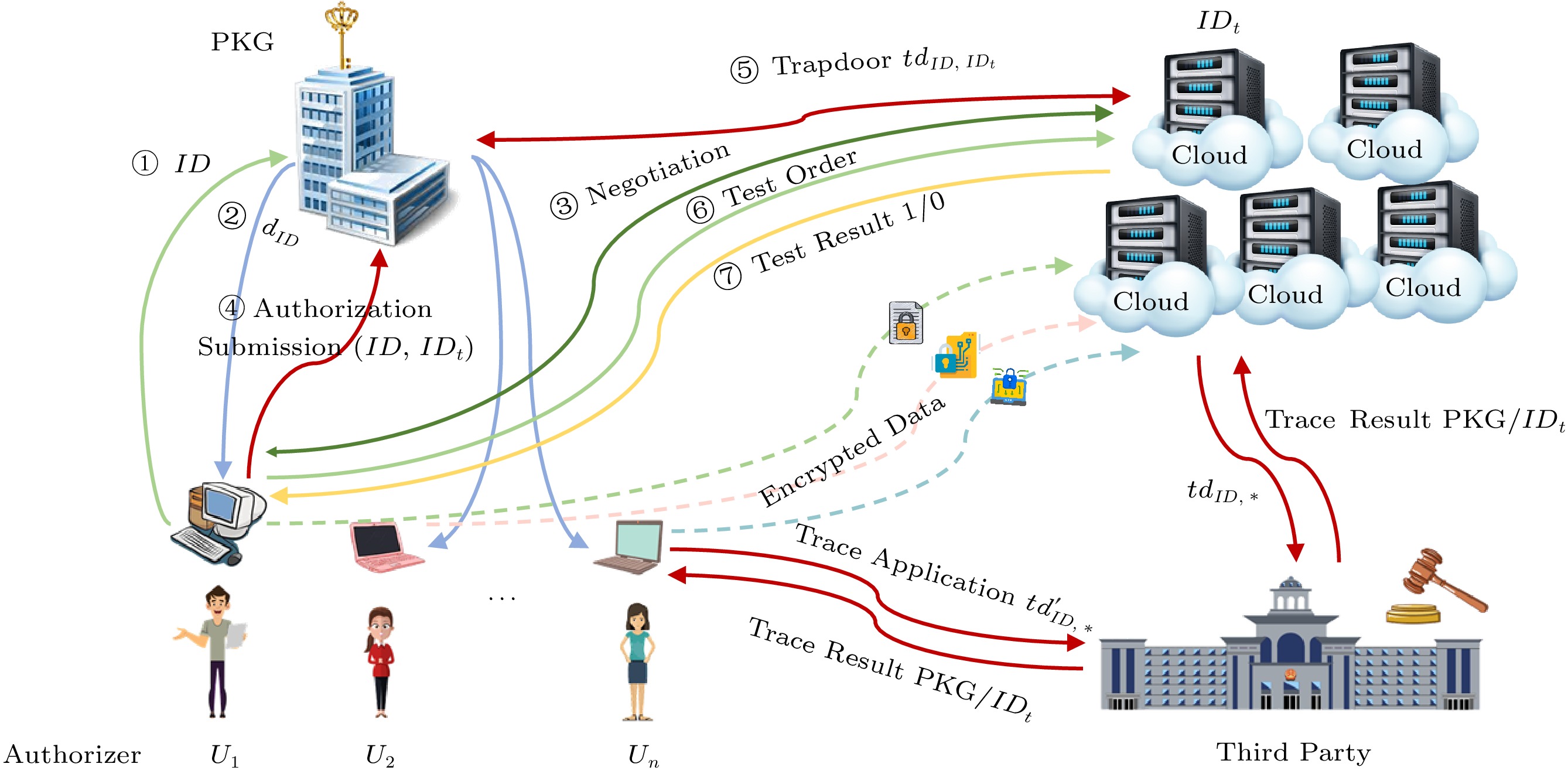
![]() System model of IBEET-AA in cloud computing. IDt: the identity of the tester. tdID, IDt: the trapdoor of the authorizer U1 with ID for the tester with IDt. tdID, ∗,td′ID, ∗: the to-be-traced trapdoor related to the authorizer U1 with ID and an unknown tester with identity ∗.
System model of IBEET-AA in cloud computing. IDt: the identity of the tester. tdID, IDt: the trapdoor of the authorizer U1 with ID for the tester with IDt. tdID, ∗,td′ID, ∗: the to-be-traced trapdoor related to the authorizer U1 with ID and an unknown tester with identity ∗.
-
![]() IND-ID-ATK game. M∗0,M∗1: two messages chosen by the adversary A. δ: information known by the adversary A when it accesses the O1 oracle. b: a random bit chosen from {0,1}. b′: the bit output by the adversary A.
IND-ID-ATK game. M∗0,M∗1: two messages chosen by the adversary A. δ: information known by the adversary A when it accesses the O1 oracle. b: a random bit chosen from {0,1}. b′: the bit output by the adversary A.
-
![]() OW-ID-ATK game. δ: information known by the adversary A when it accesses the O oracle. M∗: the challenge message chosen from the message space M. M′: the message output by the adversary A.
OW-ID-ATK game. δ: information known by the adversary A when it accesses the O oracle. M∗: the challenge message chosen from the message space M. M′: the message output by the adversary A.
-
![]() Dishonest authorizer game.
Dishonest authorizer game.
-
![]() Dishonest PKG game. ID∗: the challenge identity of the authorizer chosen by the adversary A.
Dishonest PKG game. ID∗: the challenge identity of the authorizer chosen by the adversary A.
-
![]() Dishonest tester game. ID∗: the challenge identity of the authorizer chosen by the adversary A.
Dishonest tester game. ID∗: the challenge identity of the authorizer chosen by the adversary A.
-
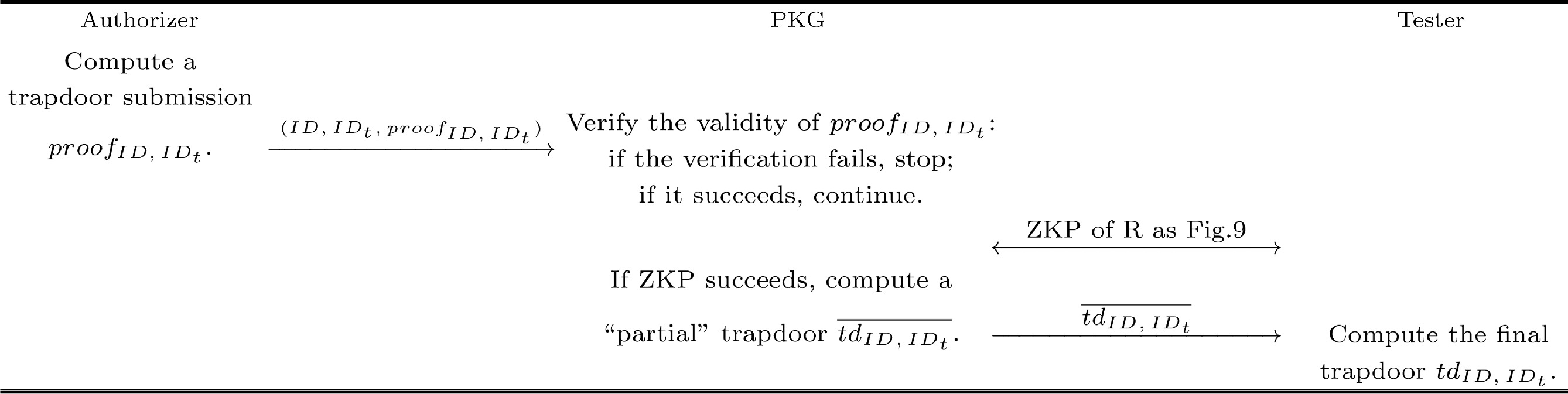
![]() Flow path of authorization protocol.
Flow path of authorization protocol.
-
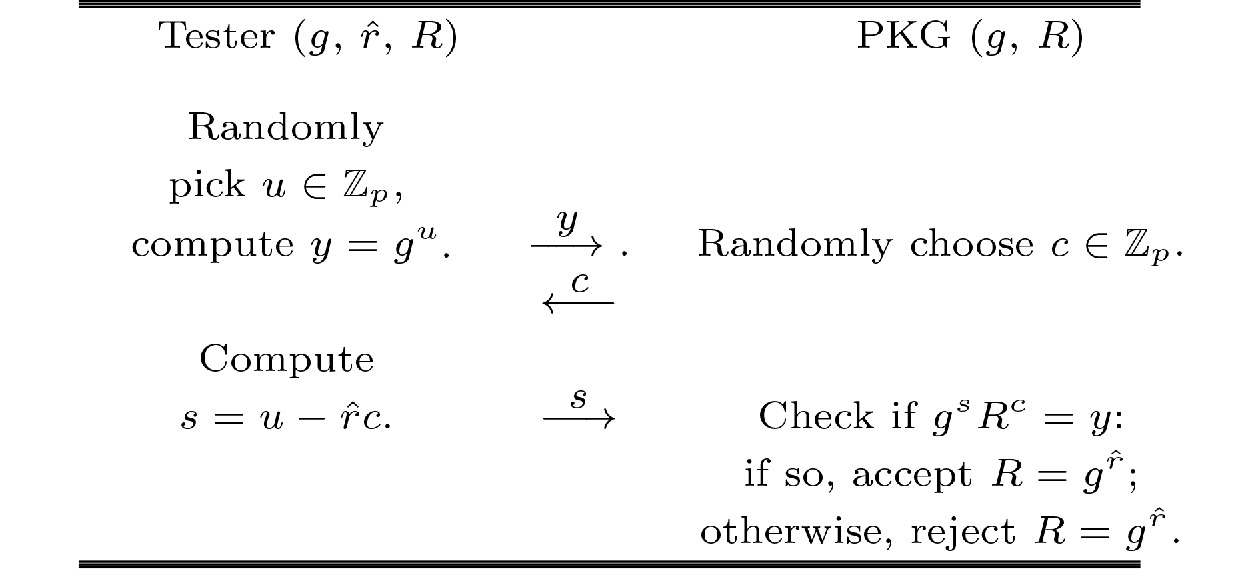
![]() Zero-knowledge proof of R.
Zero-knowledge proof of R.
-
![]() ZKP of R in dishonest PKG game.
ZKP of R in dishonest PKG game.
Others
-
External link to attachment
https://rdcu.be/eduNs -
PDF format
Highlights 157KB -
DOCX format
Chinese Information 16KB
Related articles
-
2018, 33(6): 1243-1260. DOI: 10.1007/s11390-018-1885-5
-
2008, 23(2): 166-175.
-
2004, 19(6)
-
1998, 13(3): 279-284.
-
1998, 13(3): 228-237.
-
1997, 12(2): 154-159.
-
1997, 12(1): 17-28.
-
1995, 10(5): 425-438.
-
1995, 10(3): 193-205.
-
1993, 8(2): 92-96.